IA | Information Assurance | Information assurance (IA) is the practice of assuring information and managing risks related to the use, processing, storage, and transmission of information or data and the systems and processes used for those purposes. Information assurance includes protection of the integrity, availability, authenticity, non-repudiation and confidentiality of user data. It uses physical, technical and administrative controls to accomplish these tasks. While focused predominantly on information in digital form, the full range of IA encompasses not only digital but also analog or physical form. These protections apply to data in transit, both physical and electronic forms as well as data at rest in various types of physical and electronic storage facilities. Information assurance as a field has grown from the practice of information security. |
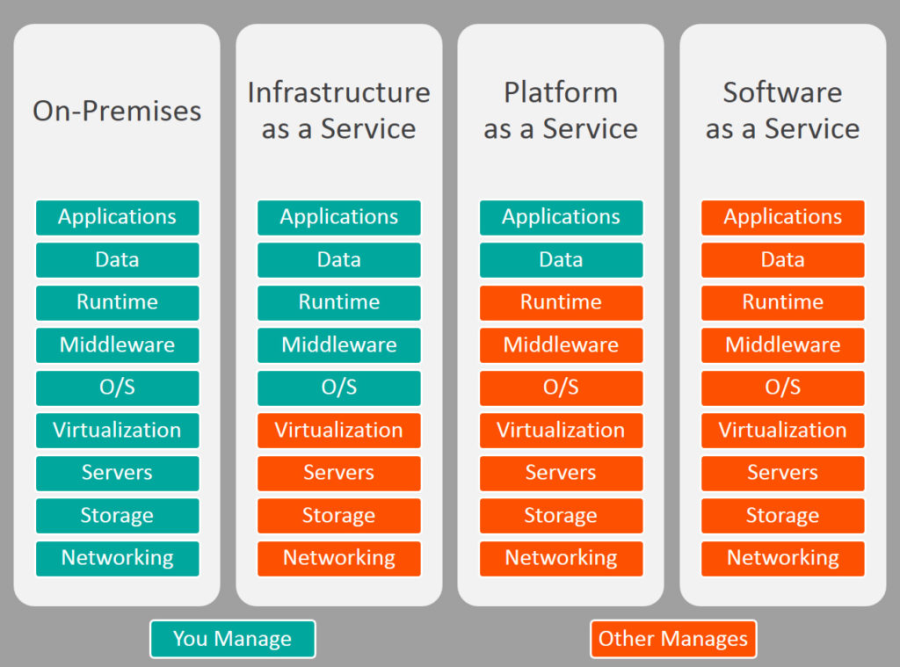
IaaS | Infrastructure as a Service | Infrastructure as a service (IaaS) is a form of cloud computing that provides virtualized computing resources over the internet. IaaS is one of the three main categories of cloud computing services, alongside software as a service (SaaS) and platform as a service (PaaS). |
ICE | Interactive Connectivity Establishment | Interactive Connectivity Establishment (ICE) is a technique used in computer networking to find ways for two computers to talk to each other as directly as possible in peer-to-peer networking. This is most commonly used for interactive media such as Voice over Internet Protocol (VoIP), peer-to-peer communications, video, and instant messaging. In such applications, you want to avoid communicating through a central server (which would slow down communication, and be expensive), but direct communication between client applications on the Internet is very tricky due to network address translators (NATs), firewalls, and other network barriers. |
ICMP | Internet Control Message Protocol | The Internet Control Message Protocol (ICMP) is a supporting protocol in the Internet protocol suite. It is used by network devices, including routers, to send error messages and operational information indicating, for example, that a requested service is not available or that a host or router could not be reached. ICMP differs from transport protocols such as TCP and UDP in that it is not typically used to exchange data between systems, nor is it regularly employed by end-user network applications (with the exception of some diagnostic tools like ping and traceroute). |
ICMPv6 | Internet Control Message Protocol version 6 (for IPv6) | Internet Control Message Protocol version 6 (ICMPv6) is the implementation of the Internet Control Message Protocol (ICMP) for Internet Protocol version 6 (IPv6). ICMPv6 is defined in RFC 4443.[1] ICMPv6 is an integral part of IPv6 and performs error reporting and diagnostic functions (e.g., ping), and has a framework for extensions to implement future changes. |
IDE | integrated development environment | a programming environment that has been packaged as an application program, typically consisting of a code editor, a compiler, a debugger, and a GUI |
IDQ | Informatica Data Quality | A tool that can be used by business analysts & developers to analyse, profile, cleanse, standardize & scorecard data in an enterprise. |
IEC | International Electrotechnical Commission | The International Electrotechnical Commission is an international standards organization that prepares and publishes International Standards for all electrical, electronic and related technologies – collectively known as "electrotechnology". IEC standards cover a vast range of technologies from power generation, transmission and distribution to home appliances and office equipment, semiconductors, fibre optics, batteries, solar energy, nanotechnology and marine energy as well as many others. The IEC also manages three global conformity assessment systems that certify whether equipment, system or components conform to its International Standards. |
IEEE | Institute of Electrical and Electronics Engineers | The Institute of Electrical and Electronics Engineers (IEEE) is a professional association with its corporate office in New York City and its operations center in Piscataway, New Jersey. It was formed in 1963 from the amalgamation of the American Institute of Electrical Engineers and the Institute of Radio Engineers. As of 2018, it is the world's largest association of technical professionals with more than 423,000 members in over 160 countries around the world.[2] Its objectives are the educational and technical advancement of electrical and electronic engineering, telecommunications, computer engineering and allied disciplines. |
IEEE 802.1ah | Provider Backbone Bridges (PBB; known as "mac-in-mac") is a set of architecture and protocols for routing over a provider's network allowing interconnection of multiple Provider Bridge Networks without losing each customer's individually defined VLANs. It was initially created by Nortel before being submitted to the IEEE 802.1 committee for standardization. The final standard was approved by the IEEE in June 2008 as IEEE 802.1ah-2008 and has been integrated into IEEE 802.1Q-2011.
| |
IETF | Internet Engineering Task Force | The Internet Engineering Task Force (IETF) develops and promotes voluntary Internet standards, in particular the standards that comprise the Internet protocol suite (TCP/IP). It is an open standards organization, with no formal membership or membership requirements. All participants and managers are volunteers, though their work is usually funded by their employers or sponsors. |
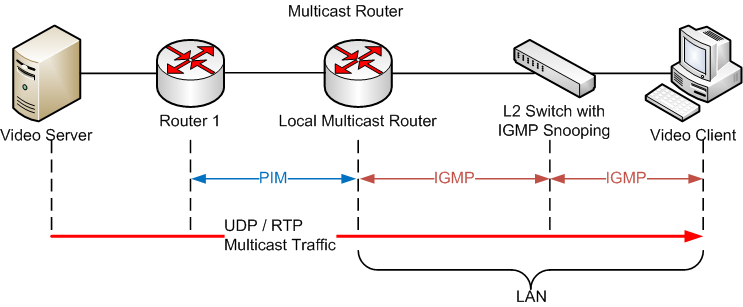
IGMP | The Internet Group Management Protocol (IGMP) is a communications protocol used by hosts and adjacent routers on IPv4 networks to establish multicast group memberships. IGMP is an integral part of IP multicast. | |
IGP | Interior Gateway Protocol | An interior gateway protocol (IGP) is a type of protocol used for exchanging routing information between gateways (commonly routers) within an autonomous system (for example, a system of corporate local area networks). This routing information can then be used to route network-layer protocols like IP. |
IGRP | Interior Gateway Routing Protocol | Interior Gateway Routing Protocol (IGRP) is a distance vector interior gateway protocol (IGP) developed by Cisco. It is used by routers to exchange routing data within an autonomous system. |
IIS | Internet Information Services | Internet Information Services (IIS, formerly Internet Information Server) is an extensible web server created by Microsoft for use with the Windows NT family. IIS supports HTTP, HTTP/2, HTTPS, FTP, FTPS, SMTP and NNTP. It has been an integral part of the Windows NT family since Windows NT 4.0, though it may be absent from some editions (e.g. Windows XP Home edition), and is not active by default. |
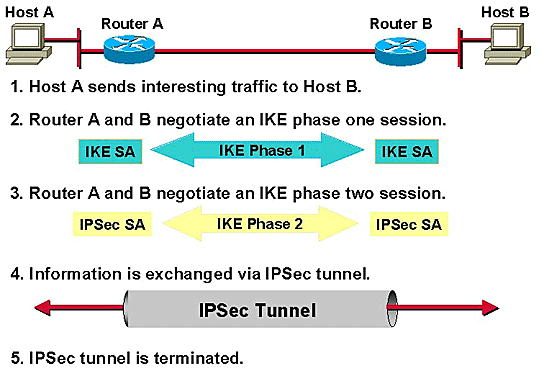
IKE | Internet Key Exchange | In computing, Internet Key Exchange (IKE, sometimes IKEv1 or IKEv2, depending on version) is the protocol used to set up a security association (SA) in the IPsec protocol suite. IKE builds upon the Oakley protocol and ISAKMP. IKE uses X.509 certificates for authentication ‒ either pre-shared or distributed using DNS (preferably with DNSSEC) and a Diffie–Hellman key exchange ‒ to set up a shared session secret from which cryptographic keys are derived. In addition, a security policy for every peer which will connect must be manually maintained. |
iLBC | Internet Low Bitrate Codec | Internet Low Bitrate Codec (iLBC) is an open source royalty-free narrowband speech audio coding format codec and reference implementation, developed by Global IP Solutions (GIPS) formerly Global IP Sound. It was formerly freeware with limitations on commercial use, but since 2011 it is available under a free software/open source (3-clause BSD license) license as a part of the open source WebRTC project. It is suitable for VoIP applications, streaming audio, archival and messaging. The algorithm is a version of block-independent linear predictive coding, with the choice of data frame lengths of 20 and 30 milliseconds. The encoded blocks have to be encapsulated in a suitable protocol for transport, usually the Real-time Transport Protocol (RTP). |
iManager | Huawei MSAN and DSLAM management tool | |
IMAP | Internet Message Access Protocol | In computing, the Internet Message Access Protocol (IMAP) is an Internet standard protocol used by email clients to retrieve email messages from a mail server over a TCP/IP connection. IMAP is defined by RFC 3501. |
Implementation | Used as a synonym for both construction and deployment. | |
Implementation Lead | Sometimes used as a synonym for construction lead and/or deployment lead. | |
Implicit Change Control | Artifacts under implicit change control are not managed directly by the CCB, but changes to the artifacts are controlled by upstream artifacts that are directly managed by the CCB. Source code is often under implicit change control. Compare to explicit change control. | |
Implicit Risk Management | Synonym for intrinsic risk management. | |
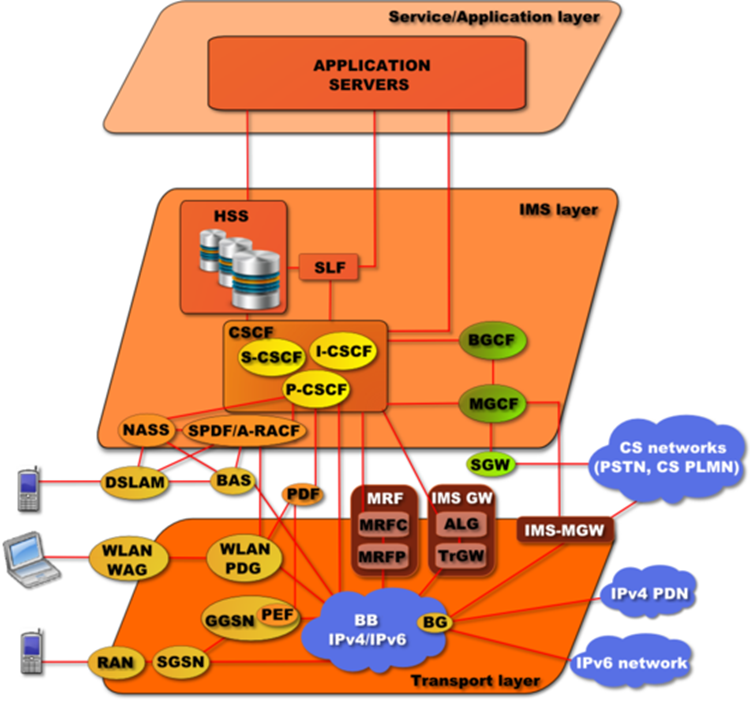
IMS | IP Multimedia Core Network Subsystem | The IP Multimedia Subsystem or IP Multimedia Core Network Subsystem (IMS) is an architectural framework for delivering IP multimedia services. Historically, mobile phones have provided voice call services over a circuit-switched-style network, rather than strictly over an IP packet-switched network. Alternative methods of delivering voice (VoIP) or other multimedia services have become available on smartphones, but they have not become standardized across the industry. IMS is an architectural framework to provide such standardization.
|
IMSI | International Mobile Subscriber Identity | The International Mobile Subscriber Identity or IMSI is used to identify the user of a cellular network and is a unique identification associated with all cellular networks. It is stored as a 64 bit field and is sent by the phone to the network. It is also used for acquiring other details of the mobile in the home location register (HLR) or as locally copied in the visitor location register. To prevent eavesdroppers identifying and tracking the subscriber on the radio interface, the IMSI is sent as rarely as possible and a randomly generated TMSI is sent instead. |
IN | Intelligent Network | The Intelligent Network (IN) is the standard network architecture specified in the ITU-T Q.1200 series recommendations. It is intended for fixed as well as mobile telecom networks. It allows operators to differentiate themselves by providing value-added services in addition to the standard telecom services such as PSTN, ISDN on fixed networks, and GSM services on mobile phones or other mobile devices. |
INAP | INAP stands for Intelligent Network Application Protocol or Intelligent Network Application Part. It is the signalling protocol used in Intelligent Networking (IN). It is part of the Signalling System No. 7 (SS7) protocol suite, typically layered on top of the Transaction Capabilities Application Part (TCAP). It can also be termed as logic for controlling telecommunication services migrated from traditional switching points to computer based service independent platform. | |
Inch-Pebble | Synonym for miniature milestone. | |
Incremental Development | In an Agile context, Incremental Development is when each successive version of a product is usable, and each builds upon the previous version by adding user-visible functionality. | |
Informal Review | Any form of review, e.g. walkthrough or desk check, other than an inspection. | |
Informal Testing | Expert judgment testing that is conducted without the use of documented test cases. Compare to formal testing. | |
information architecture | the set of ideas about how all information in a given context should be treated philosophically and, in a general way, how it should be organized; this is expressed in an information architecture document . | |
information design | the detailed planning of specific information that is to be provided to a particular audience to meet specific objectives. In one hierarchical model, the information design follows the information architecture and information planning stages. | |
Information Radiators | "Information radiator" is the term for any of a number of visual displays which a team places in a highly visible location, so that all team members can see the latest information at a glance. | |
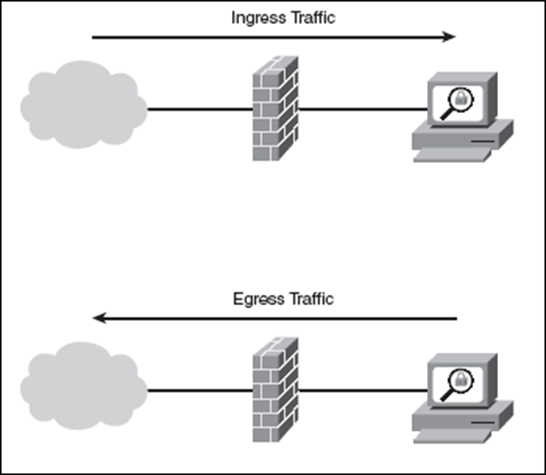
Ingress | Ingress traffic is network traffic that originates from outside of the network's routers and proceeds toward a destination inside of the network. For example, an email message that is considered ingress traffic will originate somewhere outside of a enterprise's LAN, pass over the Internet and enter the company's LAN before it is delivered to the recipient. | |
Inspection | A formally defined review process. | |
Inspector | A reviewer in the inspection process | |
Institute of Electrical and Electronics Engineers | IEEE | Electrical engineering organization whose Computer Society is the world's largest professional organization for computer and software engineers. Developers of the SWEBOK |
Integrated Development Environment | IDE | Refers to a software tool that combines one or more programming languages with editing and debugging tools. Often IDEs will also include reusable software components. |
Integration | "Integration" (or "integrating") refers to any efforts still required for a project team to deliver a product suitable for release as a functional whole. | |
Integration | The activity of combining multiple software components and making them work together. | |
Integration Test | Test focused on verifying functionality and stability of a software system or component after changes or additions. | |
International Organization for Standardization | ISO | An international organization established to promote the development of standards. |
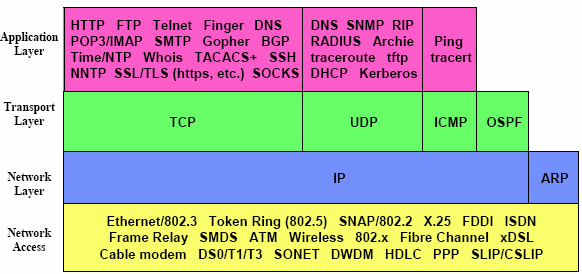
Internet Protocol Suite | The Internet protocol suite is the conceptual model and set of communications protocols used on the Internet and similar computer networks. It is commonly known as TCP/IP because the foundational protocols in the suite are the Transmission Control Protocol (TCP) and the Internet Protocol (IP). It is occasionally known as the Department of Defense (DoD) model because the development of the networking method was funded by the United States Department of Defense through DARPA. | |
Interpreted Language | An interpreted language is a type of programming language for which most of its implementations execute instructions directly and freely, without previously compiling a program into machine-language instructions. The interpreter executes the program directly, translating each statement into a sequence of one or more subroutines, and then into another language (often machine code). | |
Intrinsic Risk Management | Performing risk management as part of all project and organizational processes. Intrinsic risk management includes activities like risk-focused project and issue management and selecting lifecycles and processes that create environments which naturally manage risks. | |
INVEST | The acronym INVEST stands for a set of criteria used to assess the quality of a user story. If the story fails to meet one of these criteria, the team may want to reword it. | |
IOS cisco OS | Cisco IOS (originally Internetwork Operating System) is a family of software used on most Cisco Systems routers and current Cisco network switches. (Earlier switches ran CatOS.) IOS is a package of routing, switching, internetworking and telecommunications functions integrated into a multitasking operating system. Although the IOS code base includes a cooperative multitasking kernel, most IOS features have been ported to other kernels such as QNX and Linux for use in Cisco products or simulators such as Cisco VIRL. | |
IPS | Intrusion Prevention Services | An intrusion detection system (IDS) is a device or software application that monitors a network or systems for malicious activity or policy violations. Any malicious activity or violation is typically reported either to an administrator or collected centrally using a security information and event management (SIEM) system. A SIEM system combines outputs from multiple sources, and uses alarm filtering techniques to distinguish malicious activity from false alarms. |
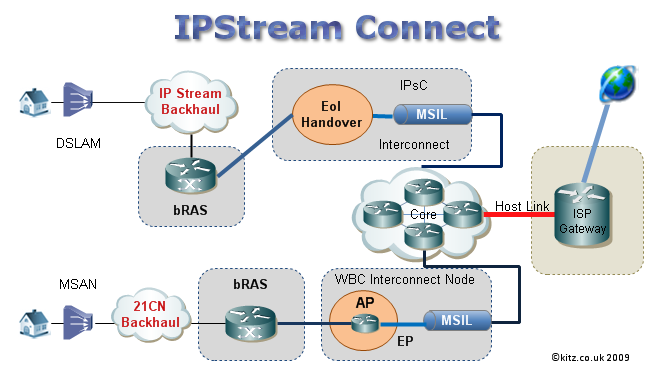
IPSC | IP Stream Connect | |
IPSec | IP Security | In computing, Internet Protocol Security (IPsec) is a secure network protocol suite of IPv4 that authenticates and encrypts the packets of data sent over an IPv4 network. Because of the complexity or immaturity of the IP security protocols, the initial IPv4 was developed without or barely with security protocols such that the IP version was incomplete, open or left for further research development. IPsec includes protocols for establishing mutual authentication between agents at the beginning of the session and negotiation of cryptographic keys to use during the session. IPsec can protect data flows between a pair of hosts (host-to-host), between a pair of security gateways (network-to-network), or between a security gateway and a host (network-to-host).[1] Internet Protocol security (IPsec) uses cryptographic security services to protect communications over Internet Protocol (IP) networks. IPsec supports network-level peer authentication, data-origin authentication, data integrity, data confidentiality (encryption), and replay protection. |
IPTV | Internet Protocol television | Internet Protocol television (IPTV) is the delivery of television content over Internet Protocol (IP) networks. This is in contrast to delivery through traditional terrestrial, satellite, and cable television formats. Unlike downloaded media, IPTV offers the ability to stream the source media continuously. As a result, a client media player can begin playing the content (such as a TV channel) almost immediately. This is known as streaming media.
|
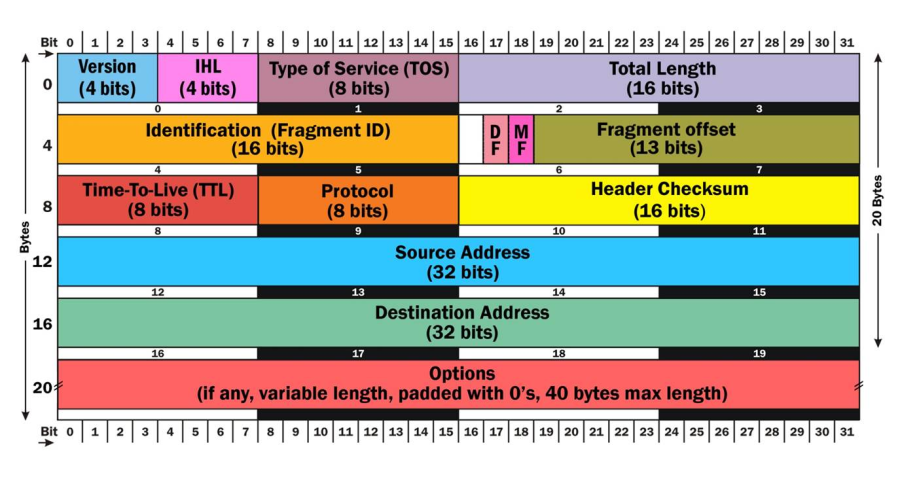
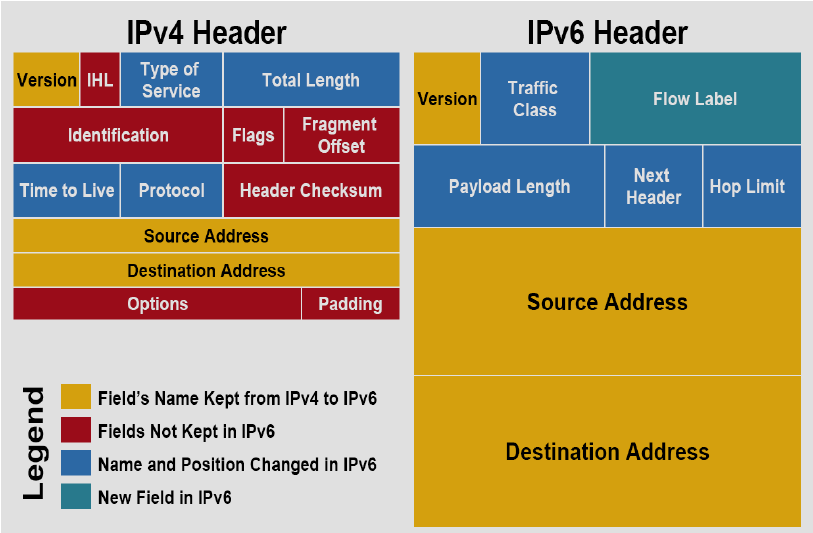
IPv4 | Internet Protocol version 6 | Internet Protocol version 4 (IPv4) is the fourth version of the Internet Protocol (IP). It is one of the core protocols of standards-based internetworking methods in the Internet, and was the first version deployed for production in the ARPANET in 1983. It still routes most Internet traffic today, despite the ongoing deployment of a successor protocol, IPv6. IPv4 is described in IETF publication RFC 791 (September 1981), replacing an earlier definition (RFC 760, January 1980). |
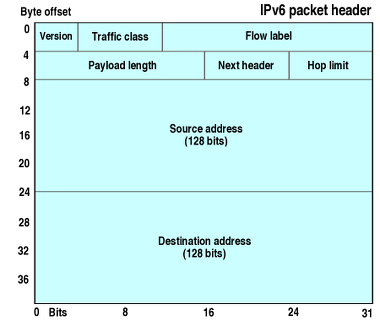
IPv6 | Internet Protocol version 4 | Internet Protocol version 6 (IPv6) is the most recent version of the Internet Protocol (IP), the communications protocol that provides an identification and location system for computers on networks and routes traffic across the Internet. IPv6 was developed by the Internet Engineering Task Force (IETF) to deal with the long-anticipated problem of IPv4 address exhaustion. IPv6 is intended to replace IPv4. IPv6 became a Draft Standard in December 1998, and became an Internet Standard on 14 July 2017. |
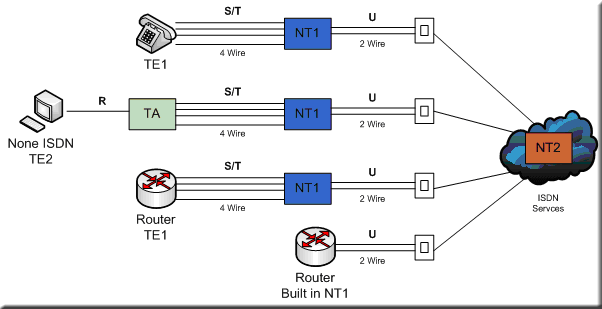
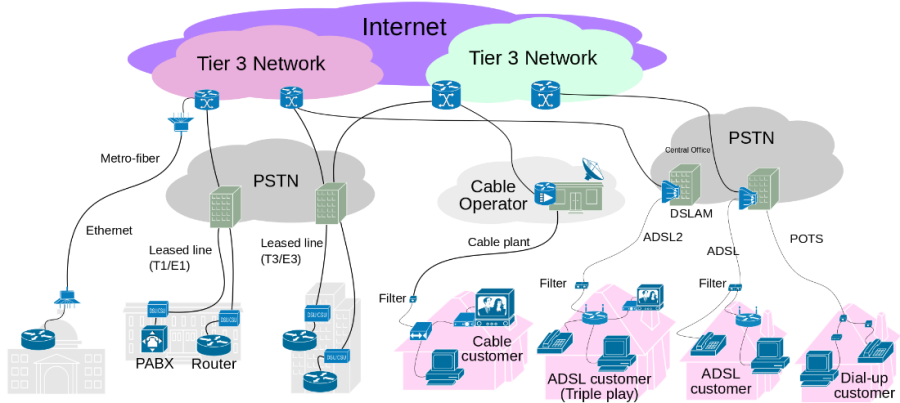
ISDN | Integrated Services Digital Network | Integrated Services Digital Network (ISDN) is a set of communication standards for simultaneous digital transmission of voice, video, data, and other network services over the traditional circuits of the public switched telephone network. It was first defined in 1988 in the CCITT red book.[1] Prior to ISDN, the telephone system was viewed as a way to transport voice, with some special services available for data. The key feature of ISDN is that it integrates speech and data on the same lines, adding features that were not available in the classic telephone system. The ISDN standards define several kinds of access interfaces, such as Basic Rate Interface (BRI), Primary Rate Interface (PRI), Narrowband ISDN (N-ISDN), and Broadband ISDN (B-ISDN). |
ISDN2BRI | Basic Rate Interface | Basic Rate Interface (BRI, 2B+D, 2B1D) or Basic Rate Access is an Integrated Services Digital Network (ISDN) configuration intended primarily for use in subscriber lines similar to those that have long been used for voice-grade telephone service. As such, an ISDN BRI connection can use the existing telephone infrastructure at a business. |
ISDN30PRI | Primary Rate Interface | The Primary Rate Interface (PRI) is a telecommunications interface standard used on an Integrated Services Digital Network (ISDN) for carrying multiple DS0 voice and data transmissions between the network and a user. |
ISO | International Organization for Standardization | The International Organization for Standardization (ISO) is an international standard-setting body composed of representatives from various national standards organizations. |
ISP | Internet Service Provider | An Internet service provider (ISP) is an organization that provides services for accessing, using, or participating in the Internet. Internet service providers may be organized in various forms, such as commercial, community-owned, non-profit, or otherwise privately owned. |
Issue | Something that needs to be resolved. | |
Issue Management | The management of issues on a project. Part of corrective activity management. | |
Issue tracker | An issue tracking system (also ITS, trouble ticket system, support ticket, request management or incident ticket system) is a computer software package that manages and maintains lists of issues, as needed by an organization. Issue tracking systems are commonly used in an organization's customer support call center to create, update, and resolve reported customer issues, or even issues reported by that organization's other employees. A support ticket should include vital information for the account involved and the issue encountered. An issue tracking system often also contains a knowledge base containing information on each customer, resolutions to common problems, and other such data. An issue tracking system is similar to a "bugtracker", and often, a software company will sell both, and some bugtrackers are capable of being used as an issue tracking system, and vice versa. Consistent use of an issue or bug tracking system is considered one of the "hallmarks of a good software team". | |
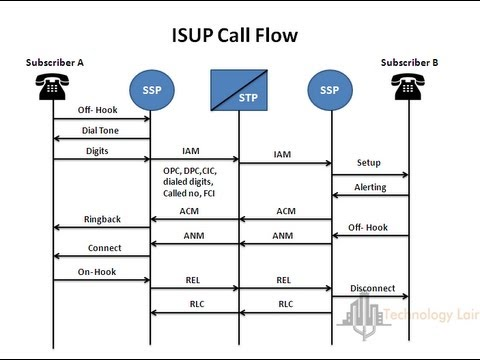
ISUP | The ISDN (Integrated Services Digital Network) User Part or ISUP is part of Signaling System No. 7 (SS7), which is used to set up telephone calls in the public switched telephone network (PSTN). It is specified by the ITU-T as part of the Q.76x series. | |
Item | Sometimes used as a synonym for CAM item; representing a change request, defect, risk, or issue. | |
Iteration | An iteration is a timebox during which development takes place. The duration may vary from project to project and is usually fixed. | |
Iterative Development | Agile projects are iterative insofar as they intentionally allow for "repeating" software development activities, and for potentially "revisiting" the same work products (the phrase "planned rework" is sometimes used; refactoring is a good example). | |
ITIL | TIL (formerly an acronym for Information Technology Infrastructure Library) is a set of detailed practices for IT service management (ITSM) that focuses on aligning IT services with the needs of business. In its current form (known as ITIL 2011), ITIL is published as a series of five core volumes, each of which covers a different ITSM lifecycle stage. Although ITIL underpins ISO/IEC 20000 (previously BS 15000), the International Service Management Standard for IT service management, there are some differences between the ISO 20000 standard, ICT Standard by IFGICT and the ITIL framework. | |
ITU | International Telecommunication Union | The International Telecommunication Union (ITU; French: Union Internationale des Télécommunications (UIT)), originally the International Telegraph Union (French: Union Télégraphique Internationale), is a specialized agency of the United Nations (UN) that is responsible for issues that concern information and communication technologies.[1] |
ITU-T | ITU Telecommunication Standardization Sector | The ITU Telecommunication Standardization Sector (ITU-T) is one of the three sectors (divisions or units) of the International Telecommunication Union (ITU); it coordinates standards for telecommunications. |
IUP | Interconnect User Part | Interconnect User Part (IUP) is a national specific Signaling System 7 protocol for interconnect between public telephone networks in the United Kingdom. This protocol was formerly known as BTNUP. |
IVR | Interactive voice response (IVR) is a technology that allows a computer to interact with humans through the use of voice and DTMF tones input via a keypad. In telecommunications, IVR allows customers to interact with a company's host system via a telephone keypad or by speech recognition, after which services can be inquired about through the IVR dialogue. IVR systems can respond with pre-recorded or dynamically generated audio to further direct users on how to proceed. IVR systems deployed in the network are sized to handle large call volumes and also used for outbound calling, as IVR systems are more intelligent than many predictive dialer systems |