DAD |
|
Disciplined agile delivery (DAD) is a process decision framework that enables simplified process decisions around incremental and iterative solution delivery. DAD builds on the many practices espoused by advocates of agile software development, including Scrum, agile modeling, lean software development, and others. |
Daily Meeting |
|
The daily meeting is one of the most commonly practiced Agile techniques and presents opportunity for a team to get together on a regular basis to coordinate their activities. |
Daily Scrum |
|
Stand-up team meeting. A plan, do, review daily session. |
Dark Fibre |
|
A dark fibre or unlit fibre is an unused optical fibre, available for use in fibre-optic communication. |
DASS1 |
|
Digital Access Signalling System 1 (DASS1) is a proprietary protocol defined by British Telecom to provide ISDN services in the United Kingdom. It is now obsolete, having been replaced by DASS2. This too will become obsolete over the coming years as Q.931, a European standard, becomes widely adopted in the EU. |
DASS2 |
|
Digital Access Signalling System 2 (DASS2) is an obsolescent protocol defined by British Telecom for digital links to PSTN based on ISDN. Although still available on request, it has been superseded by ETS 300 102 ("EuroISDN"). |
data modeling |
|
the analysis of data objects that are used in a business or other context and the identification of the relationships among these data objects. |
Data Plane |
|
See User Plane |
Database Lead |
|
Projects with large and/or critical database components may assign a database lead responsible for design and construction issues relating to the database portions of the system. |
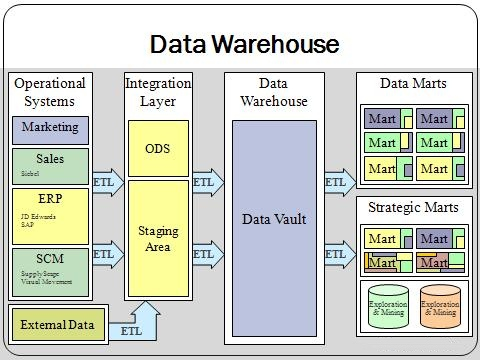
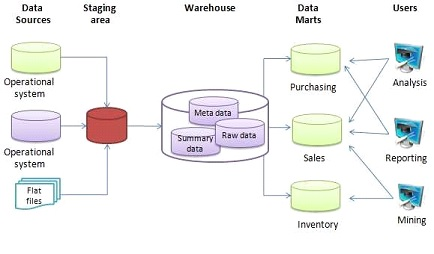
Date Warehouse |
|
In computing, a data warehouse (DW or DWH), also known as an enterprise data warehouse (EDW), is a system used for reporting and data analysis, and is considered a core component of business intelligence. DWs are central repositories of integrated data from one or more disparate sources. They store current and historical data in one single place7that are used for creating analytical reports for workers throughout the enterprise. |
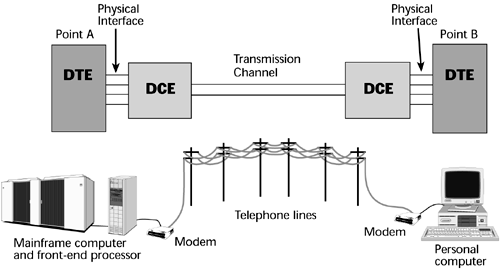
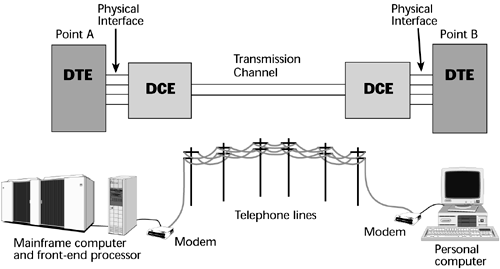
DCE |
Data Circuit-terminating Equipment |
data circuit-terminating equipment(DCE) is a device that sits between the data terminal equipment (DTE) and a data transmission circuit. It is also called data communication(s) equipment and data carrier equipment. Usually, the DTE device is the terminal (or computer), and the DCE is a modem. |
DDK |
driver development kit |
a set of programs and related files that are used to develop a new software or hardware driver or to update an existing legacy application driver for an operating system. |
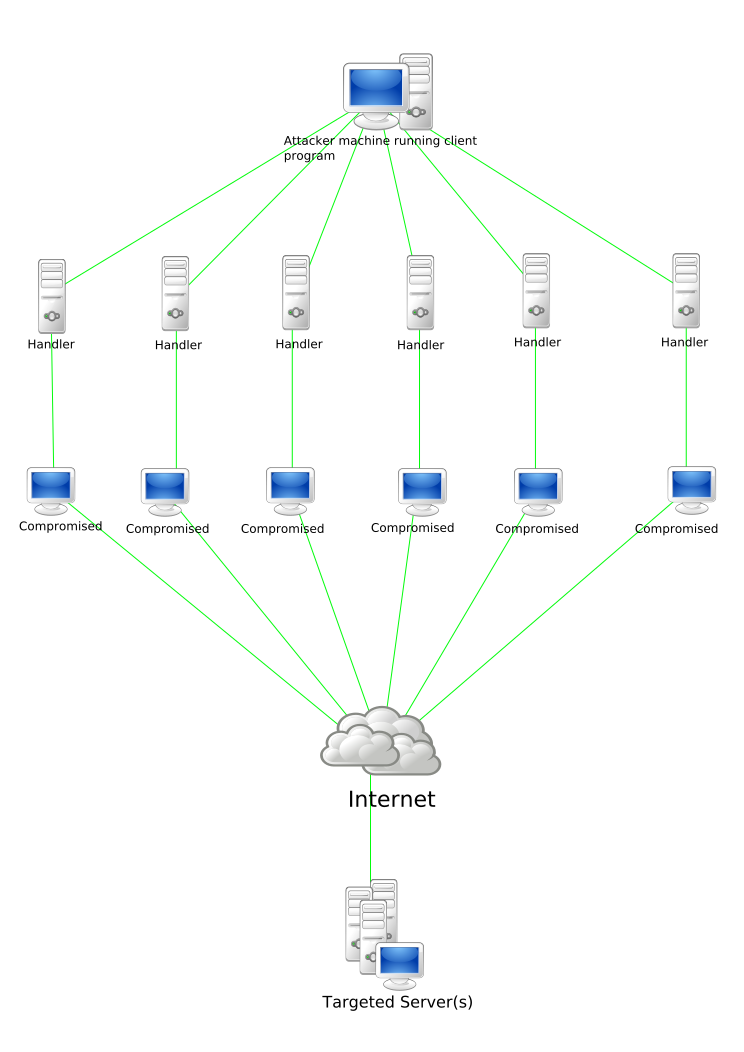
DDOS |
Distributed Denial of Service |
In computing, a denial-of-service attack (DoS attack) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. Denial of service is typically accomplished by flooding the targeted machine or resource with superfluous requests in an attempt to overload systems and prevent some or all legitimate requests from being fulfilled.[1] |
Decomposition Estimation |
|
See bottom-up estimation. Refers specifically to creating estimates for the decomposed parts of a system. |
Defect |
|
A failure of a system or process to perform as specified, or expected. |
Defect Management |
|
The representation of identified defects and the planning, tracking, and control related to ensuring all identified defects are managed. Part of both quality and corrective activity management. |
Defect Report |
|
A request to modify an artifact due to lack of conformance to a standard, requirement, project need, or a failure/error. |
Definition of Done |
|
The definition of done is an agreed upon list of the activities deemed necessary to get a product increment, usually represented by a user story, to a done state by the end of a sprint. |
Definition of Ready |
|
involves creating clear criteria that a user story must meet before being accepted into an upcoming iteration. This is typically based on the INVEST matrix. |
Deliverable |
|
Any artifact or set of artifacts that are delivered as output from a project or other well defined set of work. |
Deplhi |
|
Object Pascal refers to a branch of object-oriented derivatives of Pascal, mostly known as the primary programming language of Delphi. |
Deployment |
|
The process and/or act of installing and readying a software system for use, including integration and customization that is specific to a particular site. |
Deployment Lead |
|
Projects with complex deployment needs may assign an individual to plan and oversee execution of deployment and possibly operational and maintenance related issues. |
Deployment Plan |
|
A plan specifying the method of releasing a system. Includes items like target platforms, configuration to release, etc. |
DER |
Distinguished Encoding Rules |
ER (Distinguished Encoding Rules) is a restricted variant of BER for producing unequivocal transfer syntax for data structures described by ASN.1. Like CER, DER encodings are valid BER encodings. DER is the same thing as BER with all but one sender's options removed.
|
DES |
Data Encryption Standard |
The Data Encryption Standard is a symmetric-key algorithm for the encryption of electronic data. Although insecure, it was highly influential in the advancement of modern cryptography. |
Design |
|
Software design. The creation of abstracted models and plans for implementing requirements in software. Also denotes the design CKA. See CxStand_Design for more information. |
Design Lead |
|
Responsible for the system architecture and overseeing design activities. |
Design Pattern |
|
In software engineering, a software design pattern is a general, reusable solution to a commonly occurring problem within a given context in software design. It is not a finished design that can be transformed directly into source or machine code. It is a description or template for how to solve a problem that can be used in many different situations. Design patterns are formalized best practices that the programmer can use to solve common problems when designing an application or system. |
Design to Tools |
|
The content of a system is determined by what is directly supported by existing software tools |
Desk Check |
|
An informal review in which the author asks one or more people to read an artifact with the intent of finding defects. |
Detailed Design |
|
Commonly used term that captures parts of high level design and low level design. See CxStand_Design for more information. |
Detailed Schedule |
|
Fine grain project schedule that includes tasks, estimated effort, assigned resources, dependencies, etc. Usually created in a bottom-up fashion from a work plan. Normally implemented as a sliding window that covers a project's headlights. Compare to business schedule. |
Developer |
|
Synonym for software engineer, usually used when referring to design and construction activities. |
Developer Integration Test |
DIT |
Integration test performed by a developer in the system test environment after a project build as part of releasing functionality. |
development environment |
|
the set of processes and programming tools used to create the program or software product. |
Development Environment |
DE |
The hardware and software environment that construction work occurs in. |
development process |
|
a set of tasks performed for a given purpose in a software development project. |
DevOps |
development/operations |
bridges the gap between agile teams and operational delivery to production. |
DHCP |
Dynamic Host Configuration Protocol |
The Dynamic Host Configuration Protocol (DHCP) is a network management protocol used on UDP/IP networks whereby a DHCP server dynamically assigns an IP address and other network configuration parameters to each device on a network so they can communicate with other IP networks. A DHCP server enables computers to request IP addresses and networking parameters automatically from the Internet service provider (ISP), reducing the need for a network administrator or a user to manually assign IP addresses to all network devices. |
Diagram |
|
A graphical representation of a system, process, or other information. |
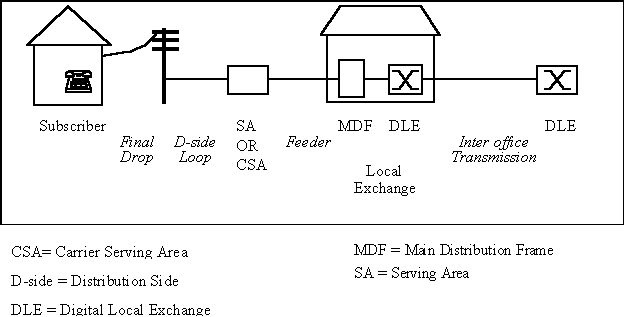
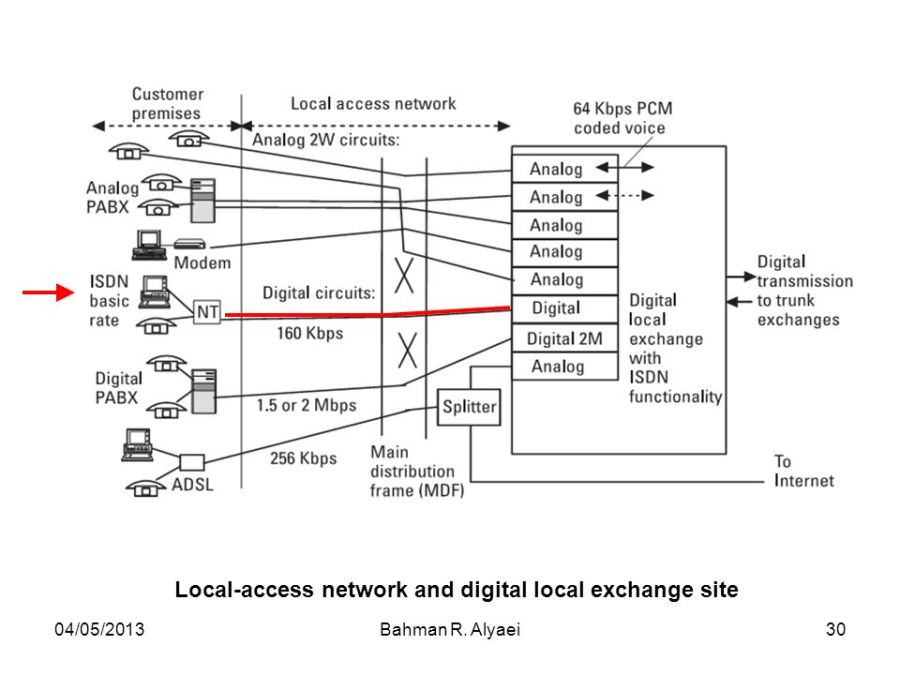
DLE |
Digital Local Exchange |
|
DLP |
Data Link Protocol |
Protocols that can be utilized at the Data Link layer of the OSI model. These protocols include token ring, FDDI, and Ethernet. Ethernet Data Link protocols are broken out into addressing and framing standards |
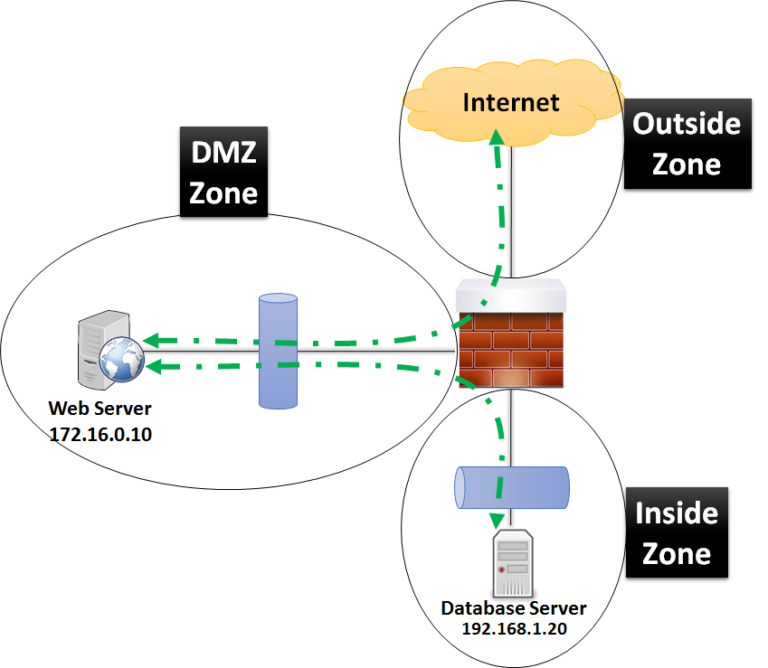
DMZ |
Demilitarized Zone |
In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted network, usually a larger network such as the Internet. The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN): an external network node can access only what is exposed in the DMZ, while the rest of the organization's network is firewalled. The DMZ functions as a small, isolated network positioned between the Internet and the private network and, if its design is effective, allows the organization extra time to detect and address breaches before they would further penetrate into the internal networks. |
DN |
Directory Number |
A telephone number is a sequence of digits assigned to a fixed-line telephone subscriber station connected to a telephone line or to a wireless electronic telephony device, such as a radio telephone or a mobile telephone, or to other devices for data transmission via the public switched telephone network (PSTN) or other private networks. |
DNB |
|
Dun and Bradstreet Business File |
DNS |
Domain Name System |
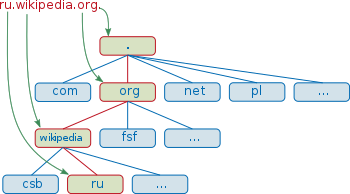
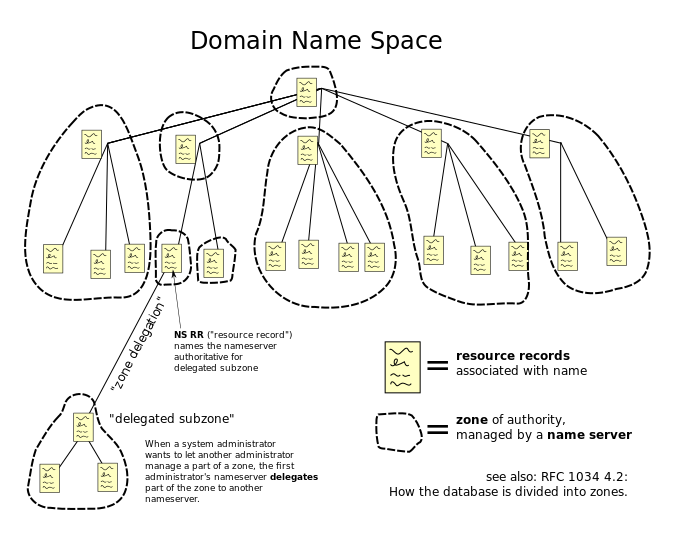
The Domain Name System (DNS) is a hierarchical decentralized naming system for computers, services, or other resources connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities. Most prominently, it translates more readily memorized domain names to the numerical IP addresses needed for locating and identifying computer services and devices with the underlying network protocols. By providing a worldwide, distributed directory service, the Domain Name System is an essential component of the functionality on the Internet, that has been in use since 1985. |
DNS - A |
IpV4 A Record |
An A record maps a domain name to the IP address (IPv4) of the computer hosting the domain. Simply put, an A record is used to find the IP address of a computer connected to the internet from a name. |
DNS - AAAA |
IPv6 DNS record |
Returns a 128-bit IPv6 address, most commonly used to map hostnames to an IP address of the host |
DNS - CNAME |
Canonical name record |
Alias of one name to another: the DNS lookup will continue by retrying the lookup with the new name. |
DNS - DNAME |
|
Alias for a name and all its subnames, unlike CNAME, which is an alias for only the exact name. Like a CNAME record, the DNS lookup will continue by retrying the lookup with the new name. |
DNS - SRV |
Service locator |
Generalized service location record, used for newer protocols instead of creating protocol-specific records such as MX. |
DNS - TXT |
Txt Record |
Originally for arbitrary human-readable text in a DNS record. Since the early 1990s, however, this record more often carries machine-readable data, such as specified by RFC 1464, opportunistic encryption, Sender Policy Framework, DKIM, DMARC, DNS-SD, etc. |
DNS Spoofing |
|
DNS spoofing, also referred to as DNS cache poisoning, is a form of computer security hacking in which corrupt Domain Name System data is introduced into the DNS resolver's cache, causing the name server to return an incorrect result record, e.g. an IP address. This results in traffic being diverted to the attacker's computer (or any other computer). |
Docker |
|
Docker is a collection of interoperating software-as-a-service and platform-as-a-service offerings that employ operating-system-level virtualization to cultivate development and delivery of software inside standardized software packages called containers.[The software that hosts the containers is called Docker Engine |
Document Collaboration |
|
Document and file collaboration are the tools or systems set up to help multiple people work together on a single document or file to achieve a single final version. Normally, this is software that allows teams to work on a single document, such as a Word document, at the same time from different computer terminals or mobile devices. Hence, document or file collaboration today is a system allowing people to collaborate across different locations using an Internet, or "cloud", enabled approach such as for Wikis such as Wikipedia |
Domain Name |
|
A domain name is an identification string that defines a realm of administrative autonomy, authority or control within the Internet. Domain names are formed by the rules and procedures of the Domain Name System (DNS). Any name registered in the DNS is a domain name. Domain names are used in various networking contexts and for application-specific naming and addressing purposes. In general, a domain name represents an Internet Protocol (IP) resource, such as a personal computer used to access the Internet, a server computer hosting a web site, or the web site itself or any other service communicated via the Internet. In 2017, 330.6 million domain names had been registered. |
Dot1Q |
IEEE 802.1Q, often referred to as Dot1q |
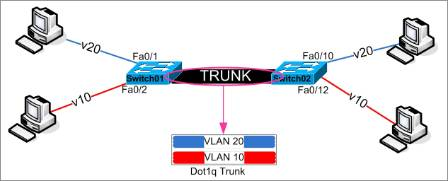
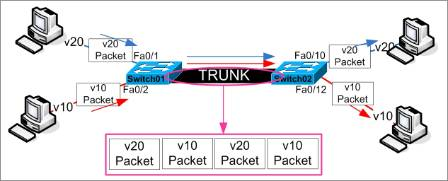
IEEE 802.1Q, often referred to as Dot1q, is the networking standard that supports virtual LANs (VLANs) on an IEEE 802.3 Ethernet network. The standard defines a system of VLAN tagging for Ethernet frames and the accompanying procedures to be used by bridges and switches in handling such frames. The standard also contains provisions for a quality-of-service prioritization scheme commonly known as IEEE 802.1p and defines the Generic Attribute Registration Protocol. |
Dot1Q trunking |
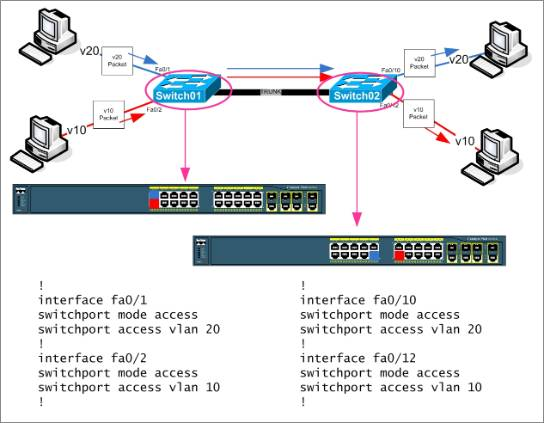
|
A simple view for dot1q (802.1q) trunking: |
Downstream |
|
In a telecommunications network or computer network, downstream refers to data sent from a network service provider to a customer. |
Downstream |
|
Used to refer to project activities and artifacts that occur later in a project lifecycle, often after significant construction has begun. Includes coding, low level design, testing, deployment, and system use. See upstream. |
DP |
Distribution Point |
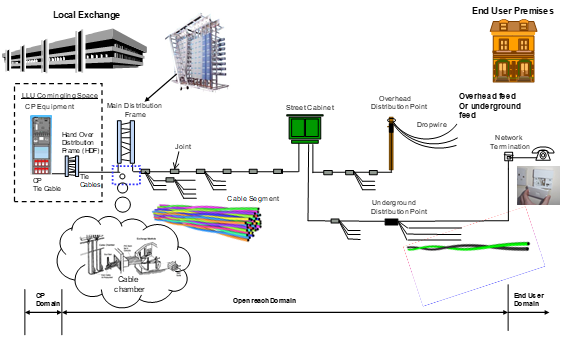
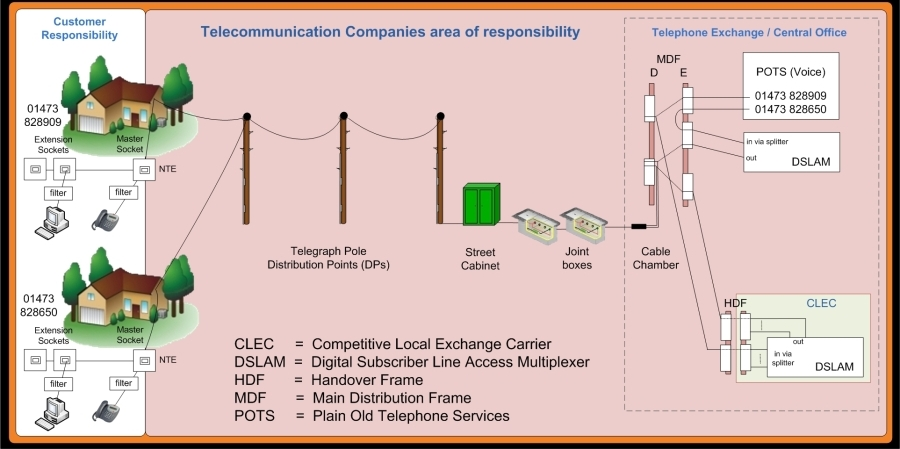
In LLU - The green termination box which is situated between the exchange and the customer premise, utilized as a junction point. |
DPI |
Deep Packet Inspection |
Deep packet inspection (DPI) is a type of data processing that inspects in detail the data being sent over a computer network, and usually takes action by blocking, re-routing, or logging it accordingly. Deep packet inspection is often used to ensure that data is in the correct format, to check for malicious code, eavesdropping and internet censorship[1] among other purposes. There are multiple headers for IP packets; network equipment only needs to use the first of these (the IP header) for normal operation, but use of the second header (such as TCP or UDP) is normally considered to be shallow packet inspection (usually called stateful packet inspection) despite this definition.[2] |
DPNSS |
Digital Private Network Signalling System |
The Digital Private Network Signalling System (DPNSS) is a network protocol used on digital trunk lines for connecting to PABX. It supports a defined set of inter-networking facilities. |
DQ |
Data Quality |
|
Draft |
|
An artifact under revision control but not yet under change control. |
driver |
|
a program that interacts with a particular device or special kind of software. The driver contains special knowledge of the device or special software interface that programs using the driver do not. |
DSCP |
Diff-Serve Code Point |
Differentiated services or DiffServ is a computer networking architecture that specifies a simple and scalable mechanism for classifying and managing network traffic and providing quality of service (QoS) on modern IP networks. DiffServ can, for example, be used to provide low-latency to critical network traffic such as voice or streaming media while providing simple best-effort service to non-critical services such as web traffic or file transfers. |
DSDM |
dynamic systems development method |
agile development methodology, now changed to the 'DSDM project management framework'. |
DSL |
Digital Subscriber Line |
Digital subscriber line (DSL; originally digital subscriber loop) is a family of technologies that are used to transmit digital data over telephone lines. In telecommunications marketing, the term DSL is widely understood to mean asymmetric digital subscriber line (ADSL), the most commonly installed DSL technology, for Internet access. |
DSLAM |
Digital Subscriber Line Access Multiplexor |
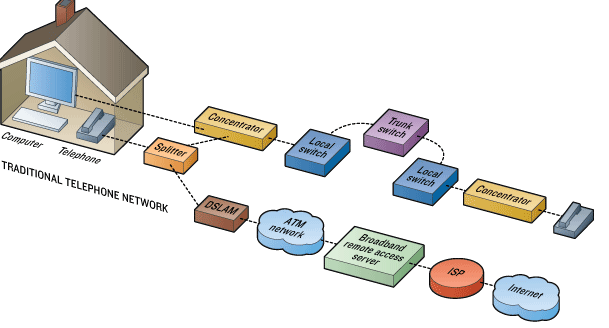
Allows telephone lines to make faster connections to the Internet. It is a network device, located near the customer's premises and connects multiple customers Digital Subscriber Lines (DSL) to a high-speed Internet backbone line using multiplexing techniques. |
DTE |
Data Terminal Equipment |
Data terminal equipment (DTE) is an end instrument that converts user information into signals or reconverts received signals. These can also be called tail circuits. A DTE device communicates with the data circuit-terminating equipment (DCE). The DTE/DCE classification was introduced by IBM. |
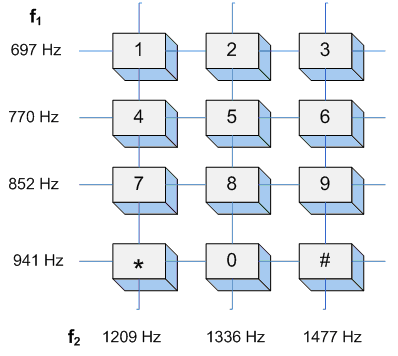
DTMF |
Dual Tone Multi Frequency |
Dual-tone multi-frequency signalling (DTMF) is an in-band telecommunication signalling system using the voice-frequency band over telephone lines between telephone equipment and other communications devices and switching centres. DTMF was first developed in the Bell System in the United States, and became known under the trademark Touch-Tone for use in push-button telephones supplied to telephone customers, starting in 1963.[1] DTMF is standardized as ITU-T Recommendation Q.23.[2] It is also known in the UK as MF4. |
DTT |
Digital Terrestrial TV |
Digital terrestrial television (DTTV or DTT) is a technology for broadcast television in which land-based (terrestrial) television stations broadcast television content by radio waves to televisions in consumers' residences in a digital format. DTTV is a major technological advance over the previous analog television, and has largely replaced analog which had been in common use since the middle of the last century. Test broadcasts began in 1998 with the changeover to DTTV (aka Analog Switchoff (ASO) or Digital Switchover (DSO)) beginning in 2006 and is now complete in many countries. The advantages of digital terrestrial television are similar to those obtained by digitising platforms such as cable TV, satellite, and telecommunications: more efficient use of limited radio spectrum bandwidth, provision of more television channels than analog, better quality images, and potentially lower operating costs for broadcasters (after the initial upgrade costs). |
DTV |
Digital TV |
Digital television (DTV) is the transmission of television signals, including the sound channel, using digital encoding, in contrast to the earlier television technology, analog television, in which the video and audio are carried by analog signals. It is an innovative advance that represents the first significant evolution in television technology since color television in the 1950s. Digital TV makes more economical use of scarce radio spectrum space; it can transmit multiple channels in the same bandwidth occupied by a single channel of analog television, and provides many new features that analog television cannot. A switchover from analog to digital broadcasting began around 2006 in some countries, and many industrial countries have now completed the changeover, while other countries are in various stages of adaptation. Different digital television broadcasting standards have been adopted in different parts of the world |
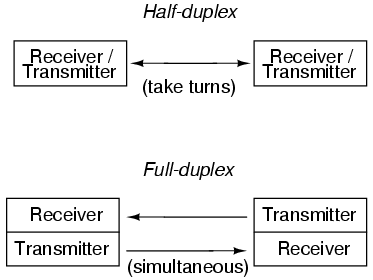
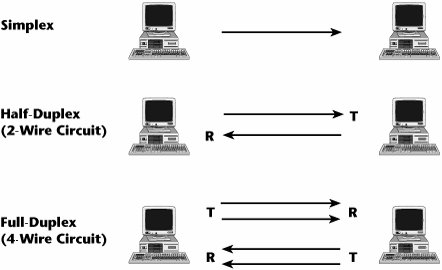
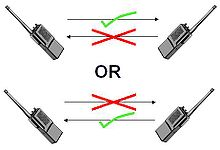
Duplex |
|
A duplex communication system is a point-to-point system composed of two or more connected parties or devices that can communicate with one another in both directions. Duplex systems are employed in many communications networks, either to allow for a communication "two-way street" between two connected parties or to provide a "reverse path" for the monitoring and remote adjustment of equipment in the field. There are two types of duplex communication systems: full-duplex (FDX) and half-duplex (HDX). |
DVSR |
Dynamically Verified Static Routing |
Dynamically Verified Static Routing (DVSR) is a proprietary routing protocol of the former Redback (now Ericsson) available on SmartEdge and Smart Services Router products. |